Single Sign-On Solution
Single Sign-On (SSO) is an identification method that allows users to access multiple applications and websites using just one set of credentials. It simplifies the login process by reducing the need to remember and enter different usernames and passwords for each service.

General
Single Sign On (SSO) solution allows users to have secure and seamless access to multiple applications and services using only one set of credentials.
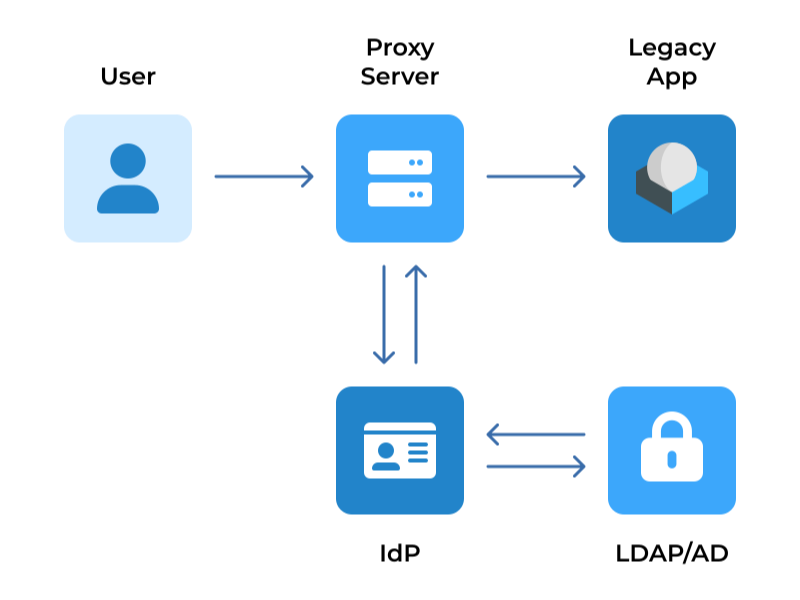
When a user signs in to a service with their SSO login, an authentication token is created and granted to the user.
Any integrated app or website the user subsequently accesses will check with the SSO, which then sends the user’s token to confirm their identity and provide them with access.
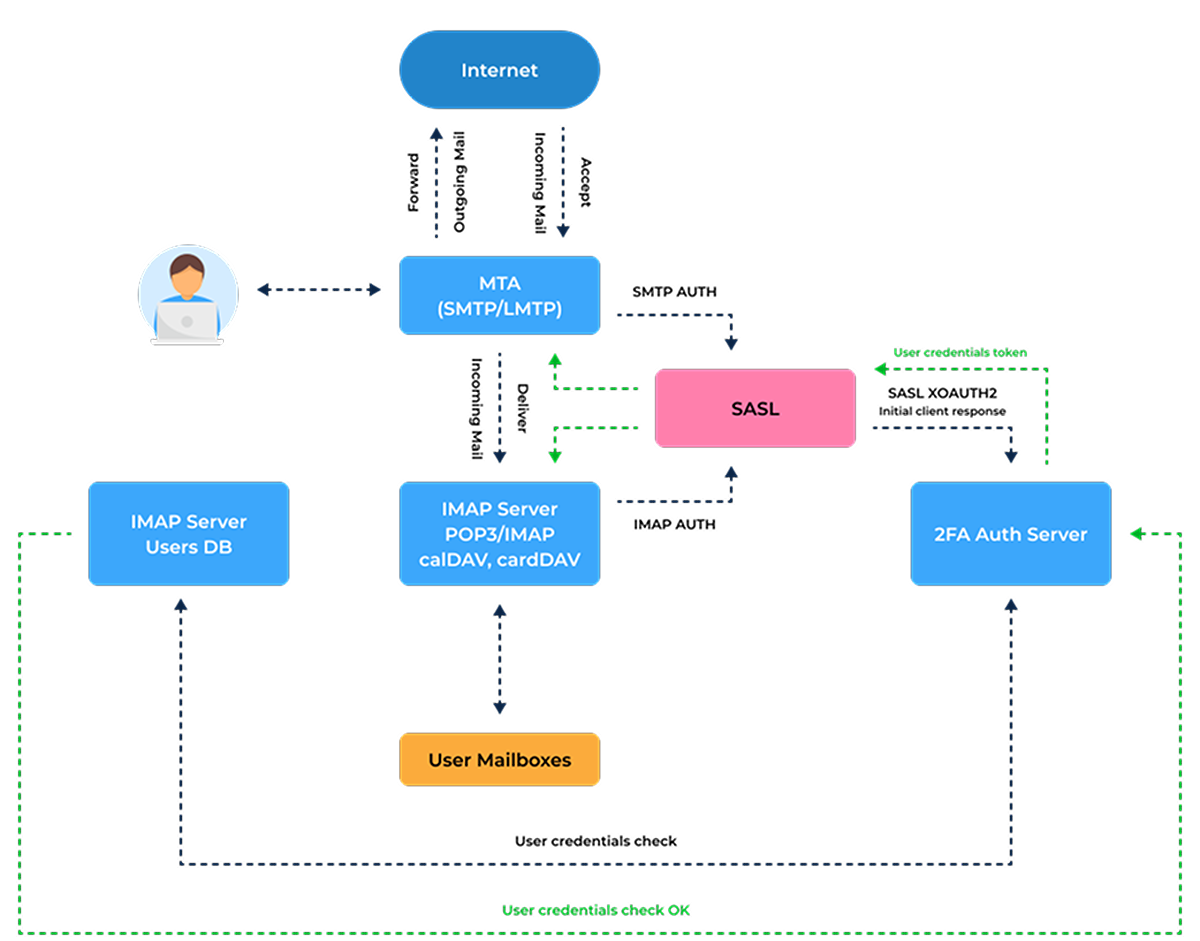
New applications can be added to SSO and customized by simply filling in configuration forms in your CRM Admin Panel.
Configurations are divided into 4 data blocks that can be saved and operated independently.
Completed forms are automatically converted to the JSON file, which can be transferred to your Identity Provider (IdP).
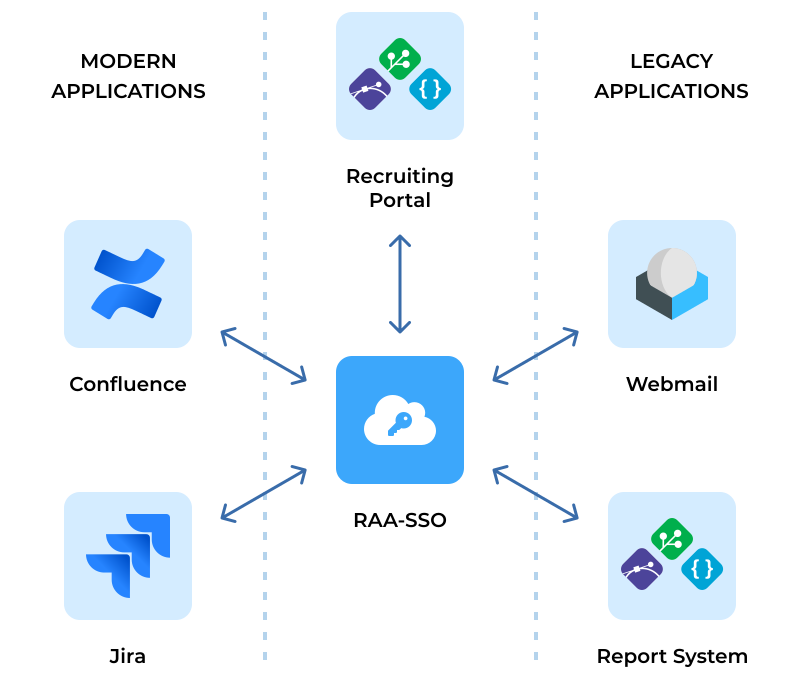
Unification
Using proxy as a middle ground, SSO solution can provide simultaneous access to modern, legacy applications and websites, ensuring users can continuously operate in all your corporate resources with no need to repeat login procedure.
We implemented this solution in our environment using forms authentication mechanism, session tokens that gets saved in browser cookies and 2-Factor Authentication (one-time password).
WordPress
We have implemented the ability to provide authentication to a WordPress admin panel of a website, using our SSO solution.
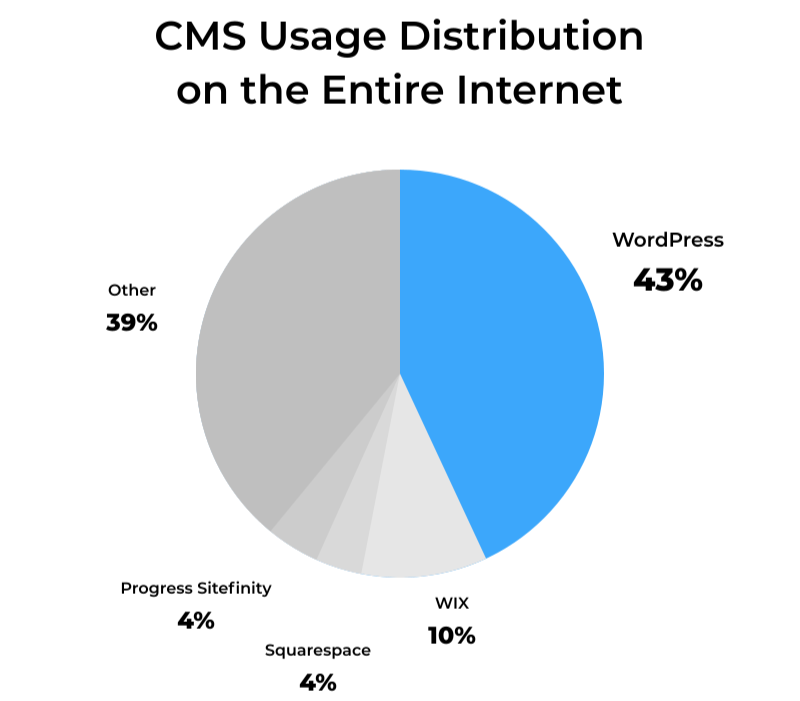
WordPress is currently the most popular Content Management System on the market.
Enhancing Security with 2FA SSH
As part of the RAA-SSO project, we’ve created a complementary system to our Single Sign-On (SSO) solution.
This system, designed to secure access to virtual machines (VMs), containers, and Git operations, uses the same credentials and two-factor authentication(2FA) as the SSO.
The result is a consistent user experience, enhanced security, and streamlined administration across different facets of your operations.
Securing VMs and containers
root@*****:/home
user@DESKTOP-KIV7C08:~$ ssh username@rightandabove.com@1.1.1.1
The combination of standard credentials with 2FA for SSH access significantly increases security, reducing the risks associated with single-factor authentication.
With a customized security module, our solution caches the 2FA after initial authentication for a set duration, balancing enhanced security with user convenience.
Our solution automates user management, linking access permissions to a central database. This simplifies administration and makes it easier to manage user permissions across multiple VMs.
When an employee leaves, their access can be revoked immediately through a single update in the central database, eliminating the need for manual changes on individual VMs.
Securing Git Operations
Secure access.
Just like with VMs, our solution requires standard credentials and 2FA for SSH access to the Git server, making unauthorized access significantly more challenging.
Dedicated security module.
Our custom-built security module verifies users when they perform operations (like clone, push, pull) on repositories, ensuring only authorized operations are allowed.
Dual-layer authentication.
With the combination of SSH keys and 2FA, our solution provides a robust level of security that protects sensitive data stored in internal Git projects from unauthorized access.

Mail Server
Our solution offers the use of MFA in calendar and address book.
Multi-Factor Authentication (MFA):
- Authentication Process
- Data Validity Period
Access to Calendar and Address Book:
- Authentication for Access
- Data Validity Check
User Reauthentication:
- Mismatched Parameters or Irrelevant Data
JSON Web Tokens (JWT) in Mail Server:
- Token Generation
- Client Compatibility
Security
- Eliminating multiple passwords reduces a common source of security breaches—users writing down their passwords
- All passwords kept in one protected, central storage
- Secure authentication with one strong password, optionally with 2-Factor Authentication
- Decreased vulnerability to phishing as users are trained to enter their password only in one corporate GUI
- SSO solution also mitigates such security risks as a user losing their corporate device, enabling administrators to instantly cut off the device’s access to accounts and critical data

Efficiency
- Higher productivity due to reduced efforts for manual authentication, password reset, and helpdesk interaction
- All network management information is stored in a single repository. This allow administrators to change user’s rights centrally ensuring that the results will propagate networkwide
- Reduce IT costs due to lower number of IT help desk requests caused by password issues
- The interface of each login step can be customized and aligned with your brand guidelines
Have questions?
We have answers.
Contact us for additional information about the company, our solutions, and more. Feel free to call or drop us an email.
Thank you for
contacting us!
We have received your message.
Your message has been received and we will be contacting you shortly to follow-up If you would like to speak to someone immediately feel free to call.