
Single sign-on (SSO) solution
Today’s world is so digitalized that the virtual world has become an integral, or to be more precise, a very important part of life. But how confident can we be that our data is completely safe?
Many of us face the daily need to visit sites, a lot of applications, and enter a lot of passwords, respectively. This creates some inconveniences because there is a possibility to type the password incorrectly, or simply to forget the password itself.
There is a standard solution for business, which closes the security holes and wraps all your legacy applications in a single solution that will help you log on with the possibility of authorization and to prevent multiple logins.
Let’s take a closer look at what the Single sign-on approach entails:
- Form-based authentication using session tokens and browser cookies is a commonly used method on websites to verify a user’s identity and provide access to secure resources. It ensures that a user’s authentication state is maintained throughout their interaction with the website. This means that by combining the use of passwords and a second factor, Single Password greatly enhances the security of user accounts, making it difficult for unauthorized individuals to access sensitive information or perform malicious actions.
- SSO software is designed not only to simplify use when navigating applications but also to minimize the work of IT administrators and developers by centralizing access control.
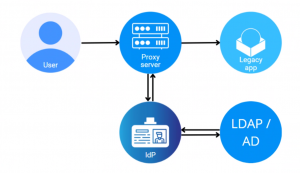
 So, below are the main benefits of SSO for business:
So, below are the main benefits of SSO for business:
- Reduce time spent re-entering passwords.
- Reduce IT costs due to a lower number of IT help desk calls about passwords.
- Reduce password fatigue from different username and password combinations.
- Mitigate risk for access to third party sites (“federated authentication”) because user-pass words are not stored or managed externally.
Every company wants to use a single scheme to secure all applications. But how about legacy applications? A lot of them are already integrated in business processes and companies don’t want to get rid of them. But they may already be out of the support cycle, or they don’t have the code base to make changes and rebuild them.
The first problem that exists with old applications and new ones is how to make sure that all the applications the company uses can use the same authentication center.
Team of Right&Above developers have created a solution to this issue by introducing one-time login and authentication and, therefore, making it so that the user doesn’t have to re-enter the password for different applications.
That is, the authentication control is provided in one place, thereby eliminating a lot of inconvenience and ensuring the safe use of all applications.
The system helps to integrate all applications into a single authentication and authorization scheme.
The second advantage is the ability to manage authentication and authorization in one place.
The third advantage is that it is possible to allow third parties to access the system while controlling access rights (view, edit, download, access to certain files, etc.).
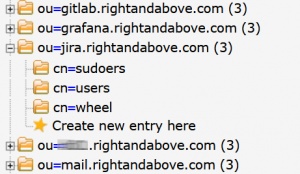 Right&Above’s SSO solution applies similar access controls to git operations over SSH. Again, a dedicated Plugable Authentication Module (PAM) has been built from scratch, providing authentication checks when users carry out operations (like clone, push, pull) that access repositories hosted on the GitLab server. To bolster security, SSH keys are used in tandem with password and two factor authentication (2FA). This arrangement ensures that sensitive data stored in internal git projects is effectively shielded from unauthorized access.
Right&Above’s SSO solution applies similar access controls to git operations over SSH. Again, a dedicated Plugable Authentication Module (PAM) has been built from scratch, providing authentication checks when users carry out operations (like clone, push, pull) that access repositories hosted on the GitLab server. To bolster security, SSH keys are used in tandem with password and two factor authentication (2FA). This arrangement ensures that sensitive data stored in internal git projects is effectively shielded from unauthorized access.
In general, Single Sign-On (SSO) provides various advantages for both users and organizations:
- Unified Access Management: The solution provides a single sign-on interface for all applications, reducing the complexity of managing multiple credentials and improving user experience.
- Legacy Compatibility: The project’s proxy solution enables legacy applications, that do not natively support modern authentication methods, to be incorporated into the SSO infrastructure without requiring modifications to their source code.
- Seamless Session Management: Users are automatically logged into all linked apps upon logging into a single application. Similarly, logging out from one signs the user out from all connected apps.
- Enhanced Security: The incorporation of 2FA and SSH keys significantly bolsters security. This two-layered approach offers robust protection against unauthorized access.
- Automated User Management: By linking access to an LDAP database, the solution allows for centralized control over users and permissions, which simplifies administration and enhances security.
- VPN-free Authentication: The proxy solution allows secure authentication with internally deployed apps without the need for a VPN connection, increasing flexibility and convenience.
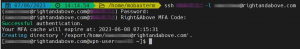
- Efficient SSH Implementation: The project eliminates the need for local users on virtual machines (VMs), reducing maintenance for administrators. SSH access is controlled via LDAP group membership and 2FA, further enhancing security.
- Simplified VM Access Management: Changes to user access rights, such as when an employee leaves the company, can be made in a single location (LDAP database), without requiring manual updates on VMs.
- Secured Git Operations: The project extends its security measures to git operations over SSH. A custom PAM module ensures only authorized users can access and manipulate Git repositories.
- Cached Authentication: The custom PAM module caches the 2FA after initial authentication for a configurable duration, reducing the need for repeated 2FA inputs and enhancing user convenience.
- Scalability: The design allows the use of any OpenID provider, ensuring the solution can be adapted to suit a variety of environments and evolve with the organization’s needs.
Overall, SSO provides a seamless and secure user experience while simplifying access management for organizations. It enhances productivity, strengthens security, and reduces the complexities and costs associated with managing multiple credentials.




















 So, below are the main benefits of SSO for business:
So, below are the main benefits of SSO for business:
 Right&Above’s SSO solution applies similar access controls to git operations over SSH. Again, a dedicated Plugable Authentication Module (PAM) has been built from scratch, providing authentication checks when users carry out operations (like clone, push, pull) that access repositories hosted on the GitLab server. To bolster security, SSH keys are used in tandem with password and two factor authentication (2FA). This arrangement ensures that sensitive data stored in internal git projects is effectively shielded from unauthorized access.
Right&Above’s SSO solution applies similar access controls to git operations over SSH. Again, a dedicated Plugable Authentication Module (PAM) has been built from scratch, providing authentication checks when users carry out operations (like clone, push, pull) that access repositories hosted on the GitLab server. To bolster security, SSH keys are used in tandem with password and two factor authentication (2FA). This arrangement ensures that sensitive data stored in internal git projects is effectively shielded from unauthorized access.